|
|





| Security and Privacy-Aware Cyber-Physical Systems |
Task 1: Platform Support
- Cyber-based approaches
- Prevention
- Detection
- sensor fusion
- timing guaranteed accountability
- Mitigation/Recovery
- Forensics
- secure synchronous provenance
- compact evidence representation for CPS
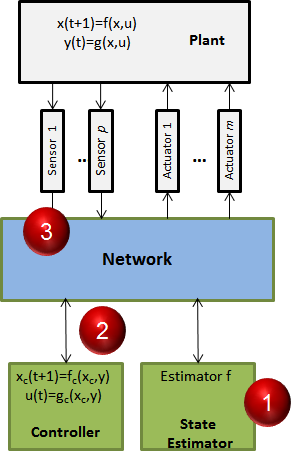
Task 2: Security-Aware Control Design
Control-level strategies:
- Robust detection and identification of sensor/actuator attacks
- Extend prior work on resilient state estimation with data-driven techniques
- Platform-aware resilient control systems
- Incorporate knowledge about the platform (e.g., communication) into control algorithm
- Control-aware cryptography
- Ensure necessary integrity of sensor data
- Avoid unnecessary overhead
|
 |
Task 3: Working with Sensitive Data
- Theme: differential privacy for CPS
- Focus areas:
- Differential privacy in distributed systems
- Exploit locality to improve privacy
- Preliminary work: differentially private resource allocation
- Privacy-related trade-offs in CPS
- Stronger privacy can reduce control performance or decrease resilience to attacks
- Security and privacy duality in control of CPS
- Preliminary work: differentially private filtering
Task 4: Security assurance for CPS
- Users resort to workarounds when they feel that security features of a system prevent them from doing their work
- Workarounds defeat security protections
- How can we predict workarounds and analyze their effects?
- Approach:
- Model potential workarounds as hazards and apply risk analysis
- Incorporate users’ mental models into model-based design of CPS
|






